Lookalike Domain Defense:
Visibility for business
impersonation protection
The distributed nature of the digital space and domain registration’s inherent flaws, make it easy for cybercriminals to register lookalike domains and carry out brand impersonation.
Lookalike Domain Defense steps in to give your business total visibility of fraudulent use of your domain, enabling you to take the necessary defensive action.
The problem Lookalike Domain Defense solves
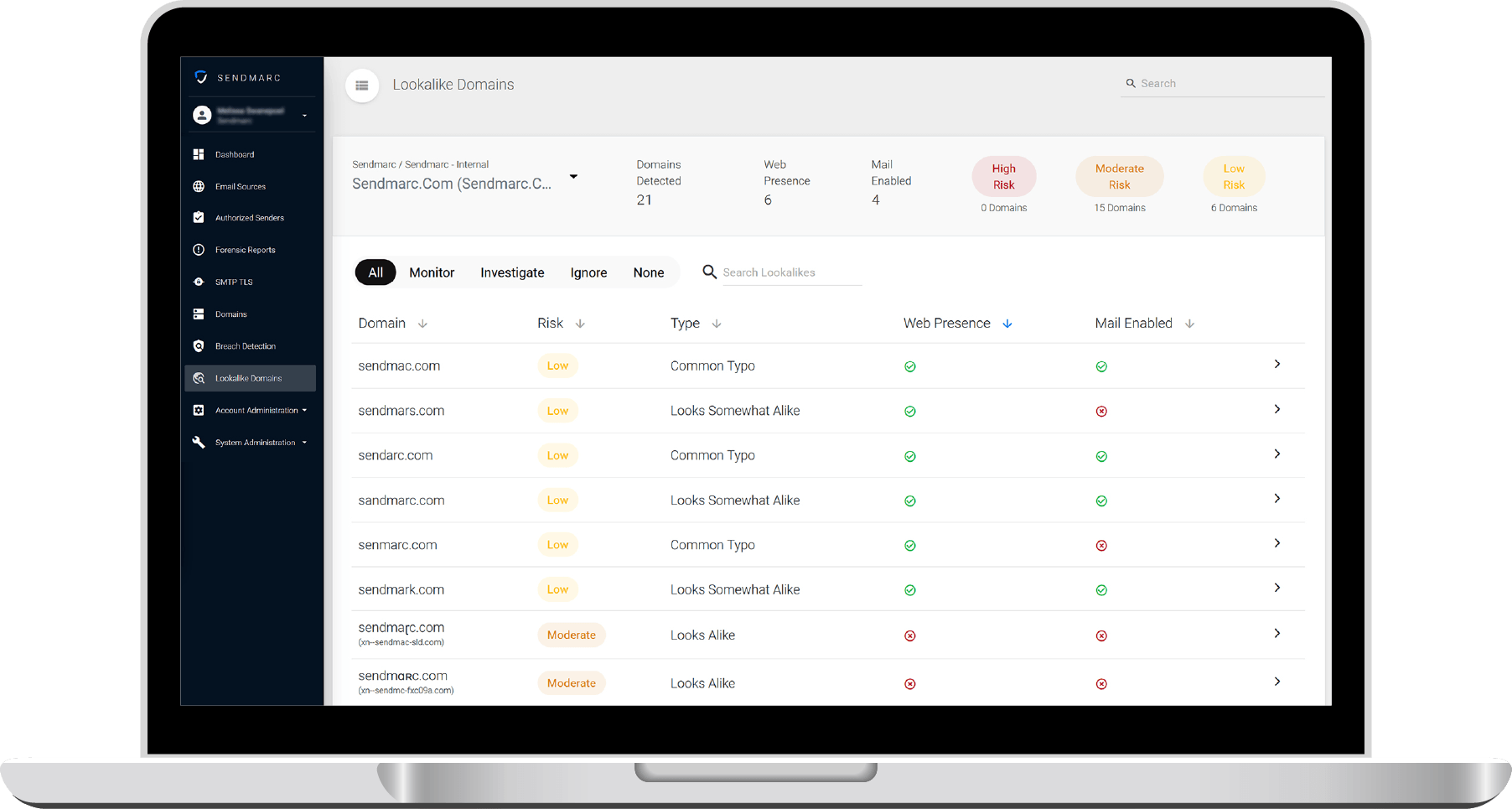
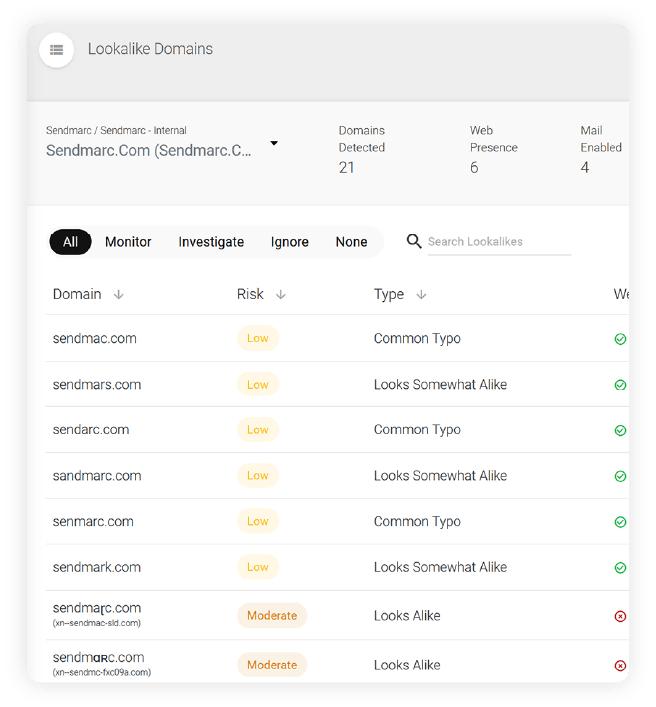
Cybercriminals use lookalike domains – domains that look extremely similar to an organization’s original domain – to carry out convincing cyberattacks where they trick users into disclosing sensitive data with fake emails or websites.
Many businesses don’t have active visibility into their lookalike domain risk, lookalike domain registrations, and brand name use.
The successful registration and use of a domain lookalike can lead to the following business damages:


Impersonation
Attackers can use lookalike domains to host websites or send impersonating phishing, spoofing, or socially engineered emails to trick employees, suppliers, and customers.


Data theft
Users are deceived into revealing sensitive information to attackers, such as personally identifiable information (PII), credit card and other financial information, or login credentials.


Reputation damage
Fraudulent use of your brand name reduces stakeholder trust in your organization and damages the good reputation you’ve worked so hard to build.


Financial loss
Lookalike domain attacks can result in direct financial loss, like the sale of fake products or services, and indirect financial losses like lost sales or reduced productivity, to name a few.


System compromise
Lookalike websites are used to distribute malware or ransomware that could grant attackers access to internal systems.
How lookalike domains are created
Cybercriminals use various techniques to create lookalike domains.
Sendmarc.com lookalike domain examples:
Lookalike Domain Defense Capabilities
Visibility of existing
lookalike domains
A watchlist of existing
lookalike domains
Notifications of new
domain permutations
Identification of web
presence
Email capability of
lookalike domains
Ready to stop sneaky imitators that are using your domain for malicious gain?
Strengthen your cybersecurity with additional
Sendmarc solutions
DMARC
DMARC is a global best practice in email
authentication that validates the legitimacy of
an email and makes sure that only real emails
reach an inbox. It gives your business full
visibility and control of outbound emails, to
ensure that no one can impersonate your
brand. Other benefits include strengthened
security, boosted deliverability, and increased
regulatory compliance.
Start for free
BIMI
Make your business’s emails stand out in
inboxes with Brand Indicators for Message
Identification (BIMI). It works with DMARC to
enable the display of your logo beside emails
in inboxes providing benefits like increased
recipient trust, improved email deliverability,
reduced phishing and spoofing attacks, and
maximized brand recognition and
awareness.
Learn more about BIMI
Breach Detection
Monitor various sources, including the
dark web, using Breach Detection to
discover if your business’s systems or
user credentials have been
compromised, and set up alerts for new
breaches. The sooner your business
knows about breached data, the faster it
can mitigate the risk and prevent
business damage.
Learn more about Breach Detection