Discover if your company data has been compromised with
Breach Detection
- Detects any system breaches
- Reveals leaked user credentials
- Regularly checks for breaches and leaked credentials
- Sends alerts about breaches (once notifications are set up)
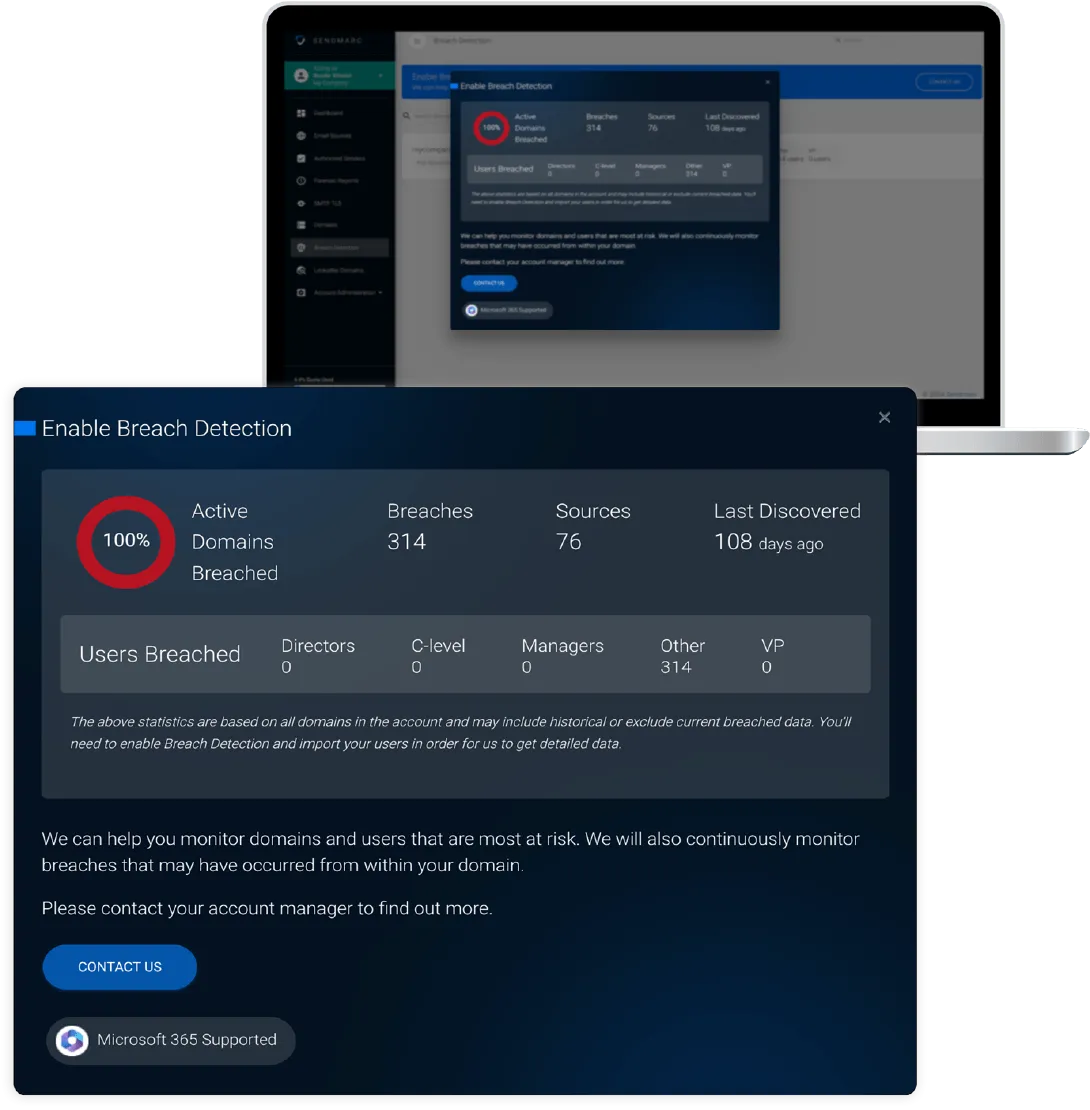
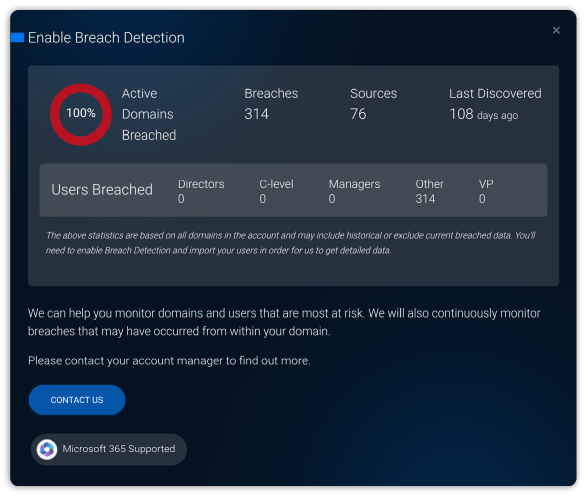
Breach Detection capabilities
The sooner your business knows about compromised data, the faster it can mitigate the risk and prevent business damage. Sendmarc Breach Detection monitors multiple sources, including the dark web to expose any information stolen or leaked from your business or its third parties including:
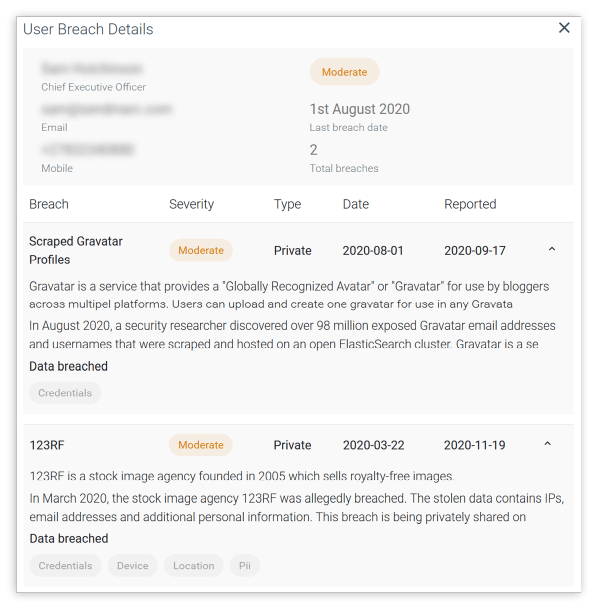
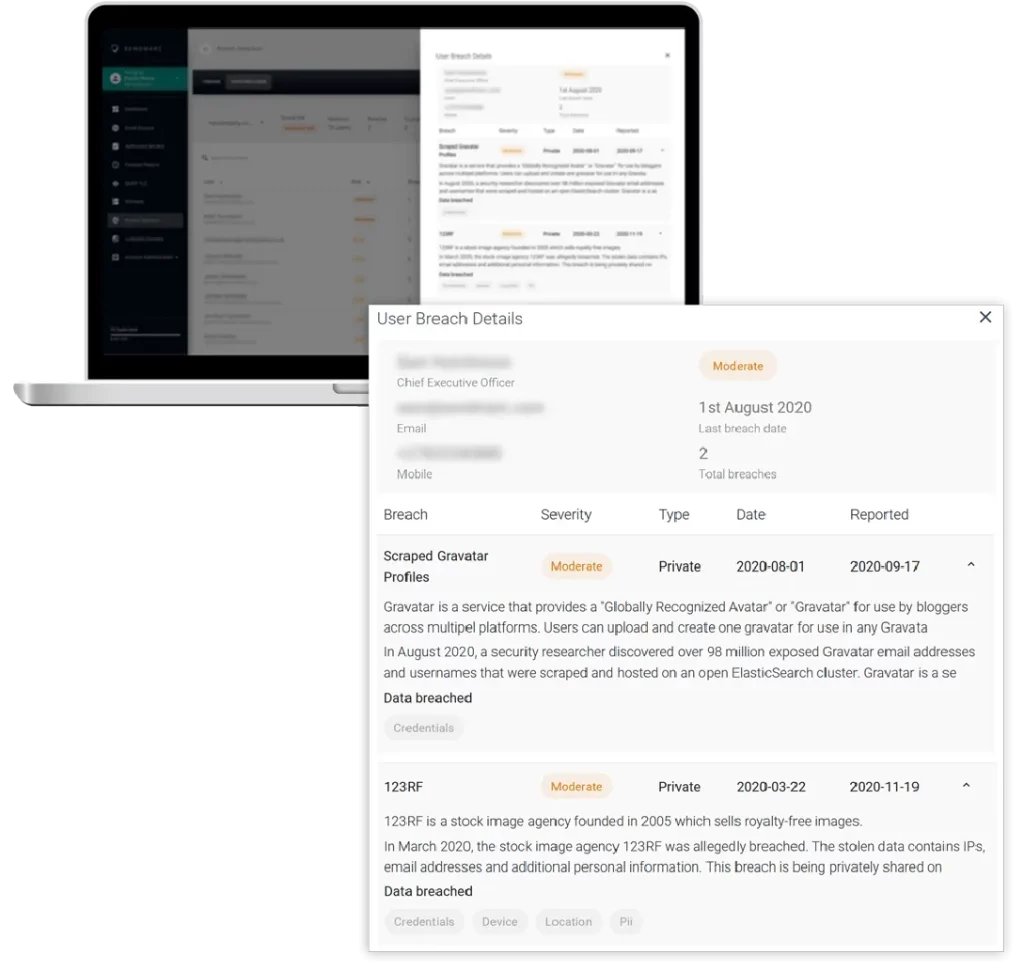
Hi-jacked credentials & personal information
Discover exposed passwords, email addresses, and other login details, as well as uncover personal employee information that’s been breached and made available on the dark web. If left unidentified, this information can be used in a cyberattack against your company, customers, suppliers, or anybody else.
Device breaches
Keyloggers and malware on personal devices – used to access work services and applications – weaken cybersecurity and threaten corporate assets. Breach Detection allows you to view data siphoned from malware-infected devices including browser history and login credentials.
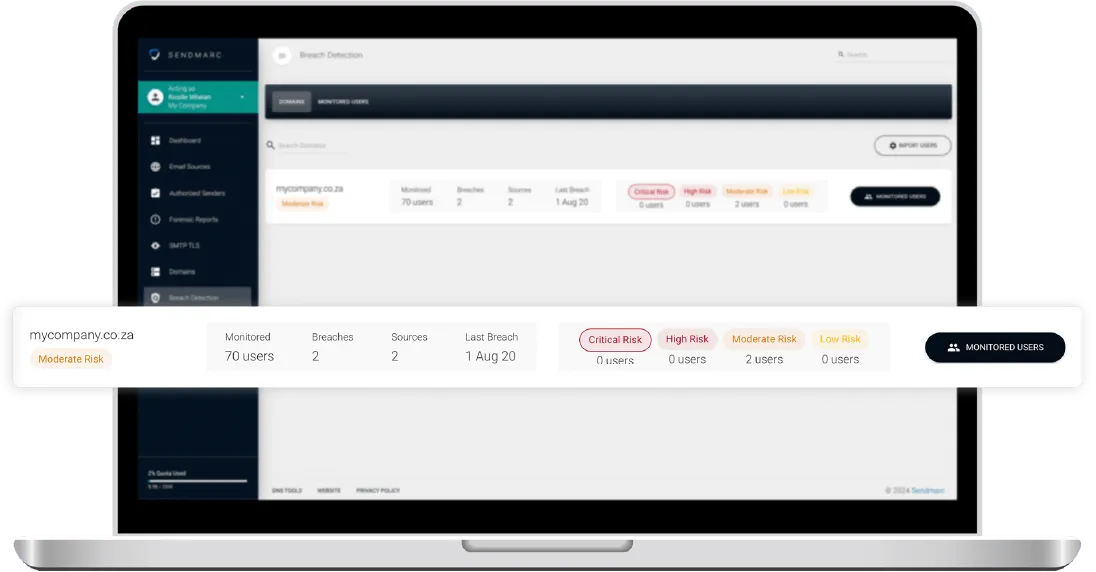
Overall breach visibility for security & compliance
From a compliance perspective, HIPAA, GDPR, and POPIA advocate that suppliers must notify customers of all breaches. Breach Detection gives your business visibility into internal or external service provider breaches affecting your business and allows you to view the sources of these breaches.
Data breaches are a 4.45 million dollar problem for large and small businesses worldwide
42 million
the number of records exposed
through data breaches between March 2021 and February 2022
$3.31 million
data breach cost
The average impact of a data breach reported by organizations with less than 500 employees
52%
of breaches involved customer PII
Making customer personal identifiable information (PII) the most breached record type
82%
of breaches involved data stored in the cloud
Either public cloud, private cloud, or across multiple cloud
environments
Source: IBM Cost of a Data Breach Report 2023
Data breach:
The business damage
Data breach:
The business
damage
It’s likely that your business doesn’t know what data cybercriminals have stolen from its employees or third parties that could impact your business. The digital nature of the Internet and cloud services in modern workspaces also leaves your organization vulnerable to breaches and credential theft.
Without further investigation, your business won’t have visibility of stolen data that can often cause damages such as:
Financial loss
The most immediate and tangible impact of a data breach is the financial loss that will be experienced by your business. This can include direct and indirect costs like fines, penalties, and legal fees, or lost revenue due to reputational damage, decreased customer trust, and business interruption.
Operational disruption
Using stolen credentials, attackers can steal data and disrupt business operations. They’re able to change, delete, or encrypt critical data, disrupting business processes, and leading to downtime, decreased productivity, and additional costs of restoring systems and processes to normal.
Environmental breach
Stolen user credentials often contain reused passwords that allow access to even the best-protected environments. Once an attacker gains access, they can work undetected for months.
Reputational damage
Your partners, customers, and stakeholders trust your business to protect their personal info and company data. A breach erodes trust in your company, ultimately resulting in lost business.
01
DMARC
Record
To use Breach Detection, your domain/s must have a verified Sendmarc Domain-based Message Authentication, Reporting and Conformance (DMARC) record. We can help you set up DMARC as quickly and simply as possible.
02
Free
Analysis
Get a free report that shows how vulnerable your company’s data is to breaches – whether that’s internally or through third-party service providers.
03
Enable Breach
Detection
Once Breach Detection is enabled, we’ll monitor your business for two weeks before providing you with a detailed report. Following this, your business can take the necessary steps for protection
Ready to resolve cybercriminal access to your company data?
Elevate your digital defenses with additional security from Sendmarc
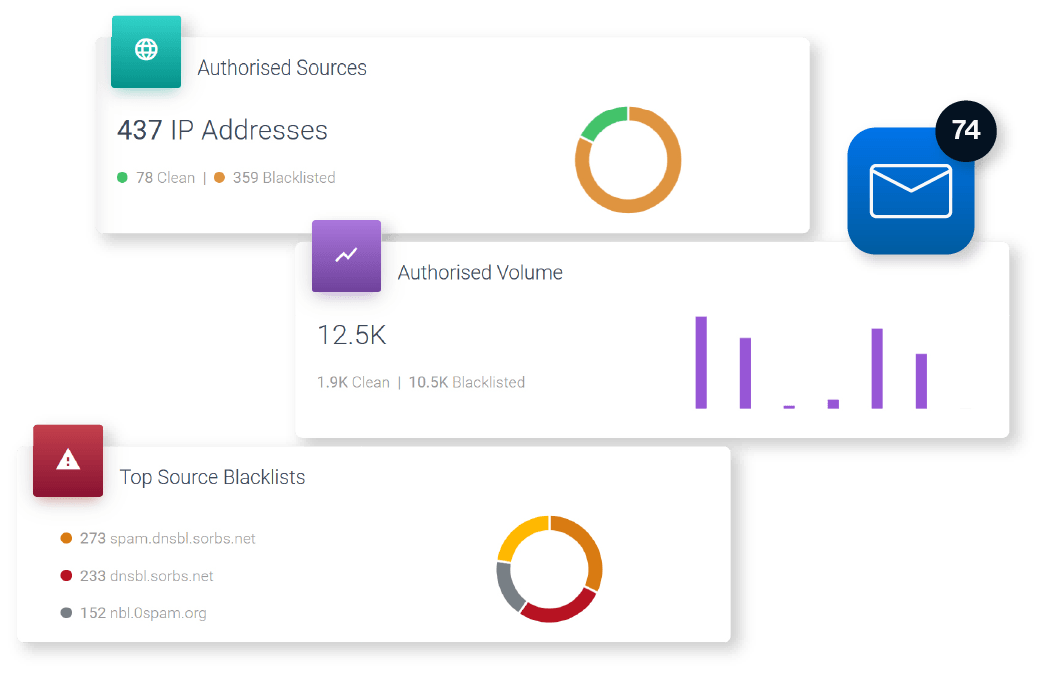
DMARC
DMARC is a global email authentication standard that verifies the source of an email and makes sure only real emails ever reach an inbox. It provides full visibility and control over emails claiming to be from your business, ultimately securing your domain against impersonation and improving email deliverability.
BIMI
Enhance brand visibility and recognition, as well as amplify the effectiveness of your emails by integrating Brand Indicators for Message Identification (BIMI) with DMARC, enabling the display of your logo beside emails in inboxes.
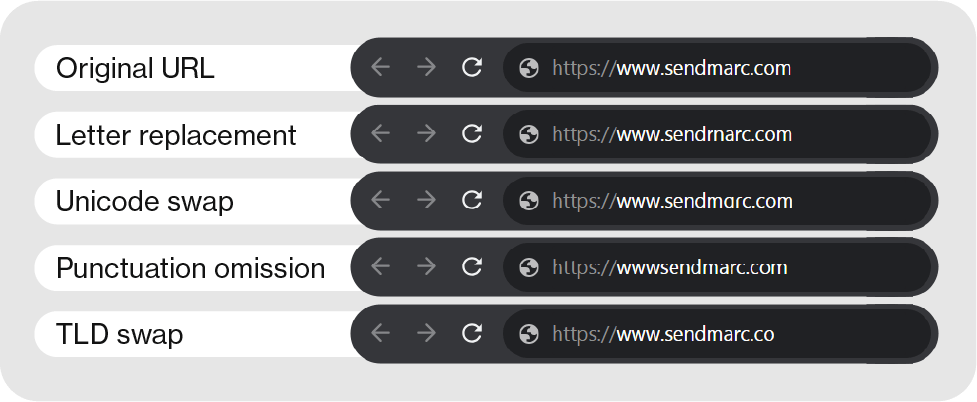
Lookalike Domain Defense
Stop cybercriminals from using imitations of your brand’s domain for malicious gain with our Lookalike Domain Defense solution. This powerful security layer lets you proactively monitor domains that resemble yours, get alerts on these, and then take the necessary action to safeguard your business against this threat.