Blog article
- 23 January 2025
- 8 minutes read

- Karyn Strybos
- Marketing Manager
BIMI boosts brand trust and protection through email authentication
With phishing and spoofing attacks on the rise and client trust being hard to earn (and keep), ensuring that your company’s customers only receive trustworthy, legitimate emails is crucial.
Enter Brand Indicators for Message Identification (BIMI), which, when combined with Domain-based Message Authentication, Reporting, and Conformance (DMARC), can help your business achieve this.
DMARC lessens the chance of your domain experiencing a successful spoofing attack. It does this by providing instructions to receiving email servers on how to handle emails that fail authentication checks.
Organizations require a DMARC policy of p=quarantine or p=reject before implementing BIMI, a standard used by companies to enhance customer trust by verifying the authenticity of their emails.
What is BIMI?
BIMI is an email authentication protocol that goes beyond traditional methods like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and DMARC. While these standards help verify the sender’s identity by validating the source and integrity of the messages, BIMI adds a visual layer, allowing organizations to display their registered trademark logos next to their emails in customers’ inboxes.
Why is BIMI important?
BIMI offers many key benefits, including:
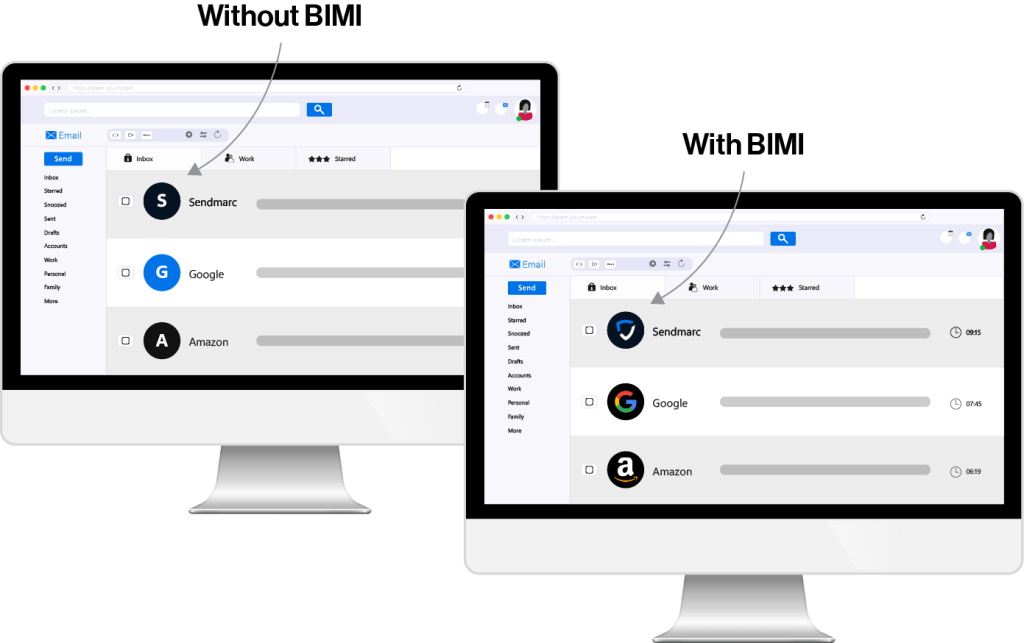
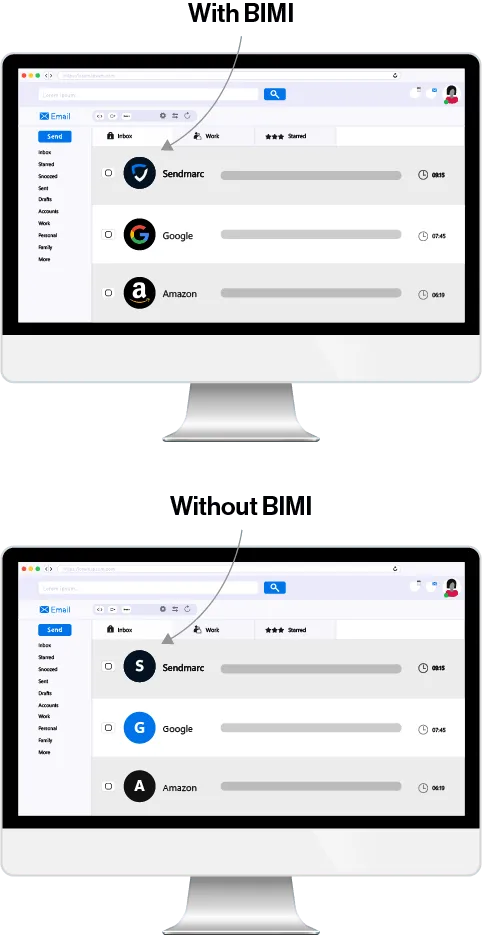
- Enhanced trust: BIMI connects your company logo to emails to authenticate them, enhancing recipients’ trust during a time when phishing is common.
- Increased visibility: Displaying your organization’s trademark in emails ensures they’re both seen and recognized as authentic.
- Improved deliverability: The credibility BIMI supplies might lead email providers to handle your business’s emails more favorably, which can improve deliverability and open rates.
- Reduced phishing risks: With BIMI, it’s harder for scammers to successfully impersonate your brand as customers might search for its logo. This cuts down the risk of a successful phishing attack, which saw almost 300 000 victims in the U.S. in 2023.
The BIMI and DMARC connection
You’re probably wondering why DMARC companies care so much about BIMI. The truth is that DMARC protects your domain against impersonation attacks, but it can’t protect against all types of email fraud on its own. BIMI complements DMARC by helping recipients quickly identify authentic messages, enhancing trust, and reducing the effectiveness of phishing attacks that might slip through filtering mechanisms.
Cybercriminals use tactics like Cyrillic characters or Unicode text to create email addresses that seem legitimate but aren’t. BIMI, when combined with DMARC, makes it harder for these threat actors to succeed, providing a dual layer of security: DMARC blocks the fake emails, and BIMI ensures recipients of the email’s authenticity.
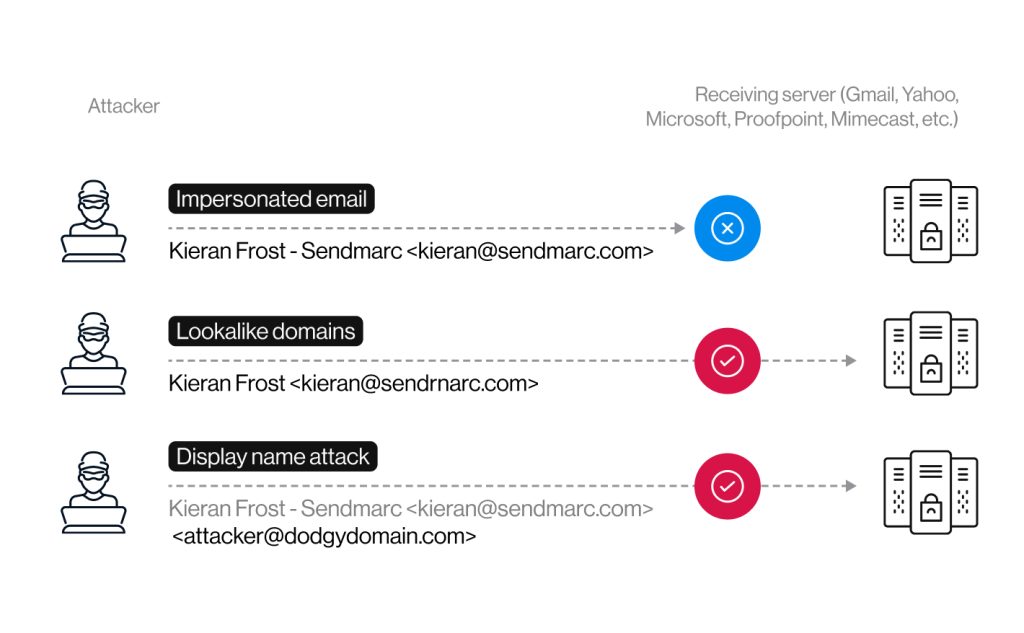
Below, we’ve included some examples of how these attacks happen.
In the first example, DMARC tells the receiving server to reject the impersonated email because it’s flagged as illegitimate. This is because the sender’s domain isn’t authorized to send emails on behalf of the actual domain.
In the second example, the attacker uses a lookalike domain that closely resembles the legitimate domain. For instance, they might use ‘sendrnarc.com’ instead of ‘sendmarc.com’. This can trick recipients into thinking the email is authentic, as they might not notice the subtle difference in the address.
The display name attack is particularly dangerous because the recipient might not hover over the sender’s email address to see the actual sender’s address. If the recipient trusts the display name (for example, “Kieran Frost – Sendmarc”), they could open the email without verifying the sender’s address.
BIMI is more than just an email enhancement
As you can see, BIMI is a powerful tool that reassures customers about the authenticity of emails they receive from your business. By adopting BIMI and DMARC, you’re not only defending against impersonation and phishing—you’re also strengthening brand trust, protection, and visibility. This is why the protocol’s growing in adoption; as of June 2024, over 21 000 domains out of the top 10 million have a BIMI record.
BIMI implementation can be a complex process compared to other protocols, but it makes up by complementing your organization’s existing email security measures. It’s a smart move to enhance trust, the foundation of many customer relationships.






